This news came out yesterday about VMWare. The company is laying off 800 people, and this includes the entirety of the Workstation and Fusion teams. This is disconcerting news to say the least. Much of the networking and security community uses Fusion/Workstation on a regular basis for testing.
I use Workstation personally to virtualize various operating systems almost daily. I do all my development inside of VM's so if something happens I can just restore from a snapshot, I don't have to worry about my laptops actual hard drive being trashed. If I read about a new vulnerability and want to test it out, I can just spin up the relevant operating system and go for it.
I will keep using workstation as long as it is viable for my needs, but I will have start shopping around for alternatives, probably either VirtualBox or QEMU.
Thanks VMWare.
f3n3s7ra
Thursday, January 28, 2016
Monday, January 25, 2016
CybatiWorks ICS pi image on windows
As part of my research concerning ICS, I stumbled across CybatiWorks, which is a ICS simulator. From their website:
The CybatiWorks™ scalable academic and professional control system cybersecurity platform enables educational institutions, industrial asset owners / operators, researchers and supporting entities to understand control system environments and cybersecurity risks. The portable and complete training platform has been validated by hundreds of industry practitioners and educators. The educational platform engages the participant in understanding, enumerating, penetrating and mitigating the engineering workstation, HMI, OPC, Historian, PLC/PAC/IED/R(M)TU/DCS and protocol communications.
Now actually getting a kit will cost you money, however they provide the VM and Raspberry Pi image on their google+ page. (You will have to be approved to join the group to download it). I don't have a Raspberry Pi at the moment, and I decided I would like to test this out before spending the money on a Pi.
Unfortunately, the Pi is ARM based, and my favorite virtualization tool, VMWare workstation doesn't support ARM. So we'll have to find another option. I settled on QEMU. Now QEMU runs natively on linux, but I don't want the overhead of running a vm inside of a vm. So first you need to install QEMU for windows which you can grab a copy of here (or you can go grab a copy from the qemu website and build from source). I used version 2.4.0, as it's a standalone executable, no install needed.
Next, we will need a ARM kernel, which can be download from here. I used the 'kernel-qemu-3.10.25-wheezy' image. Download that and put it in the same folder as QEMU.
Now we need the CybatiWorksPI.img file from their google drive. Download this and put it in the folder you installed QEMU. Warning, it's a rather large file at 7 GB.
Now we can boot the vm. Open up a command prompt and navigate to the folder where you installed QEMU and type:
qemu-system-arm.exe -M versatilepb -m 256 -cpu arm1176 -no-reboot -serial stdio -kernel kernel-qemu-3.10.25-wheezy -hda CybatiWorksPI.img -append "root=/dev/sda2 panic=1 rootfstype=ext4 rw init=/bin/bash"
This will boot the Pi image and drop us into bash:
The CybatiWorks™ scalable academic and professional control system cybersecurity platform enables educational institutions, industrial asset owners / operators, researchers and supporting entities to understand control system environments and cybersecurity risks. The portable and complete training platform has been validated by hundreds of industry practitioners and educators. The educational platform engages the participant in understanding, enumerating, penetrating and mitigating the engineering workstation, HMI, OPC, Historian, PLC/PAC/IED/R(M)TU/DCS and protocol communications.
Now actually getting a kit will cost you money, however they provide the VM and Raspberry Pi image on their google+ page. (You will have to be approved to join the group to download it). I don't have a Raspberry Pi at the moment, and I decided I would like to test this out before spending the money on a Pi.
Unfortunately, the Pi is ARM based, and my favorite virtualization tool, VMWare workstation doesn't support ARM. So we'll have to find another option. I settled on QEMU. Now QEMU runs natively on linux, but I don't want the overhead of running a vm inside of a vm. So first you need to install QEMU for windows which you can grab a copy of here (or you can go grab a copy from the qemu website and build from source). I used version 2.4.0, as it's a standalone executable, no install needed.
Next, we will need a ARM kernel, which can be download from here. I used the 'kernel-qemu-3.10.25-wheezy' image. Download that and put it in the same folder as QEMU.
Now we need the CybatiWorksPI.img file from their google drive. Download this and put it in the folder you installed QEMU. Warning, it's a rather large file at 7 GB.
Now we can boot the vm. Open up a command prompt and navigate to the folder where you installed QEMU and type:
qemu-system-arm.exe -M versatilepb -m 256 -cpu arm1176 -no-reboot -serial stdio -kernel kernel-qemu-3.10.25-wheezy -hda CybatiWorksPI.img -append "root=/dev/sda2 panic=1 rootfstype=ext4 rw init=/bin/bash"
This will boot the Pi image and drop us into bash:
f3n3s7ra
Sunday, January 24, 2016
ICS Challenge part 2
These are my attempts at the level 200 questions of the SANS ICS Challenge.
The first question is about ICS Security models.
The first question is about ICS Security models.
- In the Purdue Enterprise Reference Architecture, what level is an Operations network or manufacturing zone found at, and what level are sensors and actuators found at.
The Purdue reference model looks like the image above. The Operations network exists at level 3, and the actual sensors and actuators are on level 0.
- For the Defense in Depth model, what zone should always exist at a minimum between control systems and the internet, and unauthenticated internet accessible control systems are what?
- What are the 4 phases of the Active Cyber Defense Cycle (ACDC), and what phase has been noted to excel in ICS networks.
The first stage, Asset Identification and Network Security Monitoring is easy for ICS networks. Unlike a standard enterprise IT environment with hundreds of users on the web going out to thousands of websites, ICS networks are very static and stable, so identifying and monitoring changes is easier.
- In stage 1 of the ICS Cyber Kill Chain, what category would "Delivery, Exploit, and Install" fall into, and what is the second step in stage 2.
As we can see, "Delivery, Exploit, and Install falls into the Cyber Intrusion category. However, with an ICS compromise, landing malware on a target is often only part of the end goal, which is why there is a second stage to the kill chain.
The second step of stage 2 is the test stage.
- In the provided pcap, how many non broadcast and non multicast devices are on the network? Give MAC and IP addresses. What ICS protocol is being used, and what TCP and UDP ports are being used.
We can take a look at the protocol hierarchy to get a better idea of what's going on in the network.
So we can see multiple protocols in use-NBNS, NBDS, SMB, but the only ICS protocol being used is Modbus. Going further we can look at the list of conversations and endpoints to come up with the MAC address and IP addresses: 00:C0:82::01:0C:C2/192.168.1.3, 00:0F:73:00:76:FC:/192.168.1.200, 00:0D:9D:8D:F5:DA/192.168.1.20, 00:A0:45:C0:56:70/192.168.1.1.
The ports used in the pcap are: 80, 443, 502, 1059, 1083, 1084, 1085, 1086, 1087, 1088, 1089, 1090, 1091, 1092, 1093, 1094, 1095, 1096, 1097, 1098, 1100,1101, 1102, 1103, 1104, 1105, 1106, 1107, 1108, 1109, 1110, 1111, 1112, 1113, 1114, 1115, 1116, 1117, 1118,20562, 21811, 52340. And on UDP, 137, 138, 502,1048, 1947, 52339.
The next set of questions revolves around the Federal Energy Regulatory Commission.
- What action granted the FERC the authority to impose mandatory regulations on the electric system owners and operators as well as assess penalties. Which organization did the FERC designate as the Electric Reliability Organization. Which FERC order created the ERO CIPR standards.
We are then asked about more specifics of ICS operation.
- A control room operator interfaces with an ICS through what? Which of the following would probably make use of large scale SCADA systems: chemical plant, electric grid operation, manufacturing, warehouse distribution facility. What's the difference between SCADA and DCS. What's the difference between PLC and RTU. What's the difference between discrete, continuous, and batch processing.
The differences between SCADA and DCS arose back when bandwidth and network capacity were scarce. SCADA implied data acquisition, while DCS just implied control. However now with high speed networking the line is very blurred.
An RTU uses wireless to communicate and can be spread out across a large area They do not support control loops and algorithms. PLC's use physical media to communicate.
Continuous processing runs without interruption, typically making things like fuel, chemicals, etc. Batch processing is to make a batch of something at once, typically small to medium amounts. Could conceivable be used for drinks, medicine, food. Discrete processing is to make components of a product, like parts for cars or robots.
The next questions talk about the NERC regulations.
- What is the report filing requirement for notifying E-ISAC in the event of a reportable computer security incident. How often does the incident response plan need to be tested. How often does the identification of a bulk electric system asset need to be reviewed. How often must transmission owners perform a risk assessment.
The last question is about what to bring for an incident response:
- What should an incident response jump kit contain?
This concludes the level 200 questions for the ICS challenge.
f3n3s7ra
Saturday, January 23, 2016
ICS Holiday Challenge
I was a bit late to the party for the SANS ICS Challenge, I found out about it on the last day before it closed. SANS will be posting on their ICS blog about questions people had a lot of trouble with, but this is my attempt at the challenge. Bear in mind that since I came late to the challenge, these are not officially verified as correct.
The first question was to list 5 kinds of ICS besides SCADA. I am not an ICS expert although I am learning, so I had to research it. Although SCADA (Supervisory Control And Data Acquisition) is often used as an umbrella term for all industrial control systems, it is only one subset. The other kinds most often mention are Distributed Control Systems (DCS) and Programmable Logic Controllers (PLC). However, SANS themselves has a document on ICS, which describes several other types of control systems: Building Management Systems (BMS), Instrumentation and Control (I&C), and Safety Instrumented System (SIS). The differences between all of these categories is a little vague to me, but my best guess for question one is:
The next is about the stages of testing conducted between ICS vendors and customers. This would be the Factory Assessment Test (FAT) and Site Assessment Test (SAT). A FAT is conducted by the vendor prior to shipping the product, and they test it to make sure it meets the customers specifications. A SAT is conducted on site to make sure everything is working properly and in accordance to the specifications.
Then we are asked about the first presidential directive addressing critical infrastructure protection, and when it came out. That would be the Presidential Directive PDD-63, from May 1998.
Next we are asked to identify the information sharing organization established, how many members there are, and two of the members. The Information Sharing and Analysis Center (ISAC) is the organization, there are 24, and they include the Electricity Sector ISAC and the Emergency Management and Response ISAC.
The seventh question is identify 4 standards or regulations. These would be:
Another question asks for three examples of ICS targeted malware. The obvious one is Stuxnet, the malware which caused the destruction of Iran's nuclear centrifuges. A second example is the BlackEnergy2 malware which was used in the attacks on Ukraine's power grids. A third piece of malware would be HAVEX, which I read about in F-Secure's report.
That concludes all of the 100 point questions in the challenge.
f3n3s7ra
The first question was to list 5 kinds of ICS besides SCADA. I am not an ICS expert although I am learning, so I had to research it. Although SCADA (Supervisory Control And Data Acquisition) is often used as an umbrella term for all industrial control systems, it is only one subset. The other kinds most often mention are Distributed Control Systems (DCS) and Programmable Logic Controllers (PLC). However, SANS themselves has a document on ICS, which describes several other types of control systems: Building Management Systems (BMS), Instrumentation and Control (I&C), and Safety Instrumented System (SIS). The differences between all of these categories is a little vague to me, but my best guess for question one is:
- BMS
- I&C
- DCS
- PLC/PCS
- SIS
- Modbus
- DNP3
- EtherNet/IP
- ISO-TSAP
- HART-IP
- Modbus/TCP
- WirelessHART
- Tridium
- S7
- BACNet
The next is about the stages of testing conducted between ICS vendors and customers. This would be the Factory Assessment Test (FAT) and Site Assessment Test (SAT). A FAT is conducted by the vendor prior to shipping the product, and they test it to make sure it meets the customers specifications. A SAT is conducted on site to make sure everything is working properly and in accordance to the specifications.
Then we are asked about the first presidential directive addressing critical infrastructure protection, and when it came out. That would be the Presidential Directive PDD-63, from May 1998.
Next we are asked to identify the information sharing organization established, how many members there are, and two of the members. The Information Sharing and Analysis Center (ISAC) is the organization, there are 24, and they include the Electricity Sector ISAC and the Emergency Management and Response ISAC.
The seventh question is identify 4 standards or regulations. These would be:
- Nuclear Sector Regulation/NSR 5.71
- United States Nuclear Regulatory Commission/10 CFR US 73 and 73.54
- NERC CIP Standards/CIP 001-009
- NEI 13-10
Another question asks for three examples of ICS targeted malware. The obvious one is Stuxnet, the malware which caused the destruction of Iran's nuclear centrifuges. A second example is the BlackEnergy2 malware which was used in the attacks on Ukraine's power grids. A third piece of malware would be HAVEX, which I read about in F-Secure's report.
That concludes all of the 100 point questions in the challenge.
f3n3s7ra
Tuesday, January 19, 2016
UDP exhaustion
While I was reading through this excellent article on windows privesc, I noticed that the exploit relied on exhausting all the ports to block a DNS request. As this is something I have had to do myself on occasion, I wrote up a quick script for binding to all the ports and dropped it on my github.
F3n3s7ra
F3n3s7ra
Tuesday, January 12, 2016
SANS Holiday Challenge Walkthrough part 3
The /etc/hosts file in the firmware gave us this ip address: 52.2.229.189 . In the game we ask tom and and he answers that yes it is in scope, just don't cause a DoS. Running a shodan search against the IP gives us:
It looks like it's an AWS instance with port 80 open running a web service. It has a distinctive header "X-Powered-By: GIYH::SuperGnome by AtnasCorp" which we can use to search for the other SuperGnomes. Sure enough shodan finds several more of them:
- 52.64.191.71, Sydney Australia
- 52.34.3.80, Boardman, United States
- 52.2.229.189, Ashburn, United States
- 54.223.105.81, Brazil
- 52.192.152.132, Tokyo, Japan
We can then log in with the admin credentials we pulled from the database. And there's the first gnome.conf
One down, 4 to go.
f3n3s7ra
Monday, January 11, 2016
SANS Holiday Challenge Walkthrough part 2
After completing the first part of the challenge, you are instructed to download the gnome's firmware. Now we can use binwalk and the firmware-mod-kit to unpack this. If the firmware mod-kit is not already on your system, a quick "apt-get install firmware-mod-kit" will install it. Running "binwalk -e firmware.bin" will extract the firmware.
We can see that there's a squashfs file system, which binwalk will have automatically extracted for us.
Running cat etc/*release shows us that the OS is OpenWRT.
We can determine the architecture the OS was built for by running the file command on any binary in the firmware dump.
We can see it's a 32 bit LSB built for ARM. The /etc/hosts file contains a reference to a "supergnome." This allows us to answer the first question: "what OS and CPU type are used in the gnome"-it's an ARM CPU running OpenWRT.
Digging through the www folder we see package.json, and opening it there are references to express-eg express.js, a node.js framework, as well as to MongoDB. With this we can answer the question "what web framework is the gnome interface built in," the gnome interface is built on NodeJS using ExpressJS.
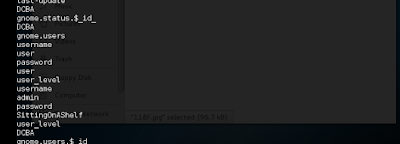
We know that the web framework references MongoDB, so there's a good chance that's what is installed. We find several files in /opt/mongodb. Running "strings *" on them gives us this output:
And there's the Admin password in clear text which lets us answer the last question "what database engine runs the gnome web interface and what is the password"
F3n3s7ra
Sunday, January 10, 2016
SANS Holiday Challenge Walkthrough part 1
I missed was traveling with my family over Christmas and New Years and didn't have a chance to post these yet, this is part 1 of the 2015 SANS Holiday Challenge. This year SANS released an entire 8 bit game which places you in the Dosis neighborhood where you solve a series of challenges.
After getting the pcap from Josh Dosis, opening it up in Wireshark gives us:
Going to Statistics>Protocol Hierarchy show that many of the packets are DNS.
After getting the pcap from Josh Dosis, opening it up in Wireshark gives us:
Going to Statistics>Protocol Hierarchy show that many of the packets are DNS.
Filtering the pcap to only show DNS reveals that it is all TXT requests. DNS TXT records are used to store extra information about a host, but they are also a covert way to transfer data-eg DNS tunneling. One of the more popular tools to do this is iodine.
Inspecting the hex dump of the packet, it seems that the part of the TXT record we're interested in is Base64 decoded, as shown by the double =.
SANS provides a python script which you are intended to modify to pull out the payload, but tshark will do it easily:
tshark -T fields -Y dns -e dns.txt -r gnome.pcap | while read txt; do echo $txt | base64 -d; done
The first question was "what commands were sent across the gnomes C&C channel." The answer to that is evident in the first several lines of the output here: The commands executed were "iwconfig" and "cat /tmp/iwlistscan.txt"
Farther down, the output dissolves into unprintable characters. But just before that it says that the file "/root/Pictures/snapshot_CURRENT.jpg" was being transferred. So now we need to carve the jpg out. A simple "binwalk -e output" extracts the jpg giving us:
Which is the answer to the second question, "What image appears in the file sent across the C&C by the Dosis gnome."
f3n3s7ra
Thursday, January 7, 2016
Spawning a pty from a php shell
Earlier today, I was performing a test, had dropped a php shell on the web server and gotten a reverse shell. Everything was working great, only one problem. I couldn't execute su or sudo, or ssh. Tring brought up this error:
su: Must be run from a terminal
A simple way to get around this is to use a scripting language to spawn a pty:
echo "import pty; pty.spawn('/bin/bash')"> /tmp/shell.py
python /tmp/shell.py
This results in a standard terminal where you can run any binary.
f3n3s7ra
su: Must be run from a terminal
A simple way to get around this is to use a scripting language to spawn a pty:
echo "import pty; pty.spawn('/bin/bash')"> /tmp/shell.py
python /tmp/shell.py
This results in a standard terminal where you can run any binary.
f3n3s7ra
Subscribe to:
Comments (Atom)