The third part of the challenge starts out by giving us this hash: 392afaed9e68dd857d15072d8646c51a
- What type of file is this, what campaign was using this malware, what 0-day was used in this campaign, what is another hash associated with this campaign, what are at least C2 addresses observed as part of this campaign.
Next we are asked to conduct another analysis of the pcap.
- There is an obvious ICS protocol being used, what are the status codes it is using. At one point this protocol communicates about tags set on the system, what are these tags? There is an indication of an ICS protocol in use on another segment of this network. what is this protocol?
Then looking farther down at the actual content of one of the packets we can see one of the status codes the question asks about.
So now we can go and look for the rest of these status codes, there are in total: Read Holding Registers (3), Read Input Registers (4), Read Coils (1), Unknown Function (103), Unknown Function (104), Unknown Function (105), Unknown Function (120), Unknown Function (121), and Unknown Function (122).
Now we need to find the tags. Most of the modbus packets are either Read Holding Function or Read Input Registers, neither of which carry much in the way of data that we'd be interested in. However the Unknown Function packets have a large blob of data, let's start looking through those. And bingo!
We see the status codes GREEN and RED. Upon more digging we see the codes OPEN and CLOSE as well.
As I was going through the packet capture, some NBNS requests stood out to me.
These are NetBIOS Name Service lookups for sites like Netflix and Amazon. Leaving aside the issue of employees trying to visit those sites, this points to another interesting fact. NBNS is used to try to resolve a domain, AFTER a DNS lookup fails. Now I didn't see any DNS packets in the capture, meaning it's probably not running in the environment. However this provides an opportunity for malicious attackers on the network to employ NBNS spoofing, without even having to go through the trouble of exhausting the UDP ports to block DNS first.
I do not know enough about ICS protocols to try to discern what the other protocol being used on a different network segment is.
The next set of questions is about internet connected ICS.
- How many modbus devices are currently connected to the internet in North America. How many BACNet clients are currently connected to the internet in the US. How many IEC-104 devices are online currently. Document a feature of Shodan that you find interesting.
Now we do the same thing for BACNet:
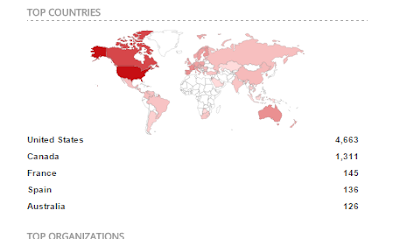
And we see that there are 4,663 BACNet devices connected to the internet. And then we do this once more for IEC-104:
Which returns 109 currently connected devices. Lastly we are to document a feature of Shodan that we find interesting. To me, that would be the Shodan API, which let's you utilize the power of Shodan in your own applications.
That was the final 300 level question.
f3n3s7ra






No comments:
Post a Comment